Ransomware is not something that you can take lightly. Today, when most of your confidential/personal data is stored online, we can’t afford to have it compromised in any form. And we can’t have someone else access it and then, restrict us from accessing our own data. Then, you are expected to pay a hefty ransom to get your data back. This is how businesses can collapse and lose it all. And if you think that this is a minor issue and not worth your time, consider this instance from 2017.
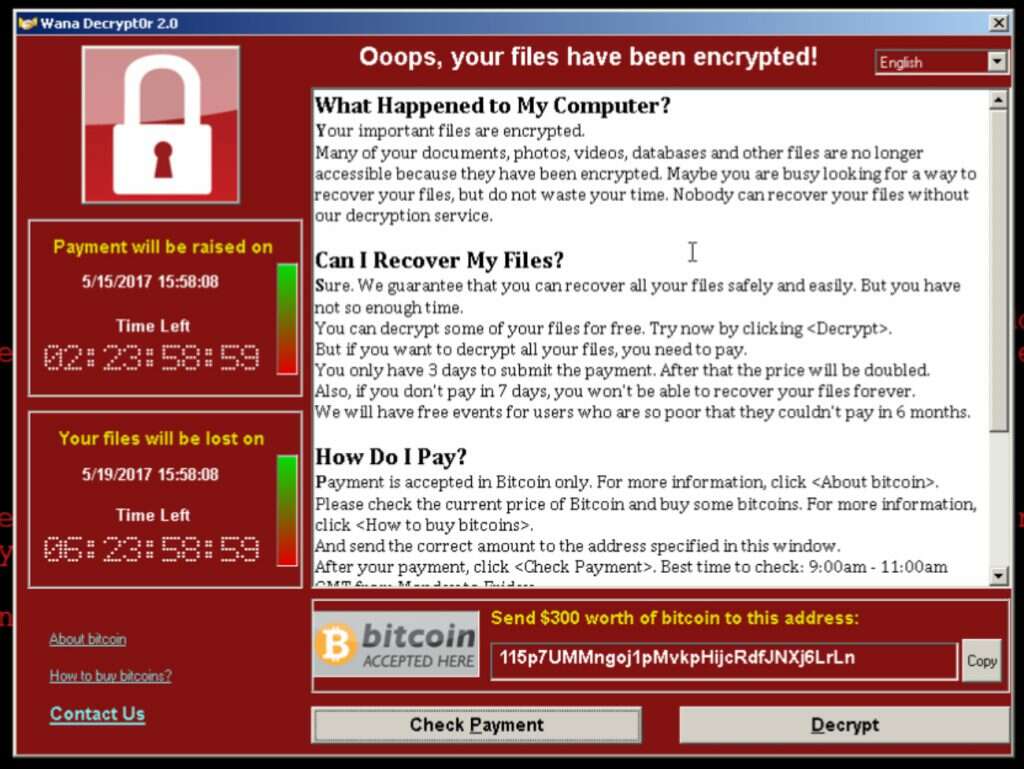
On May 12th 2017, the world witnessed the biggest ever cyber terrorism in the Internet history (even bigger than the Dyn DDoS). A ransomware named WannaCry shook the web, with the damage epicenter being in Europe. WannaCry malware charged a susceptibility on Windows OS, first discovered by the NSA, which was revealed to all of us by the Shadow Brokers.
In the first few hours, 2 lakh machines were infected by this ransomware. It was first reported from Sweden, Britain and France, but Russia and Taiwan were the worst hit, according to US media. Huge brands including Renault, FedEx, Telefonica and the NHS were among the victims and were outright crippled by the attack.
What is ransomware?

Ransomware, also known as Business Email Compromise, is a type of malicious software and part of cyber terrorism that infects a computer and restricts users’ access to it until a ransom is paid to unlock it. Individuals and organisations are discouraged from paying the ransom, as this does not guarantee that access will be restored. If reports are to be believed, this malware had globally caused a loss of a whopping $3 billion to the companies.
What is cyber terrorism?
According to many anti-cyber-terrorism experts, Cyber terrorism is any intentional, unethically motivated attack against high-end data, computer systems, user information, computer programs and sensitive data records which results to cause intensive harm to the cyber terrorist targets.
Today, the threat of cyber attacks and attempts of unethical tactics of hackers are higher than ever. In spite of all the stringent laws formed to combat cyber terrorism taken forth by authorities; fighting against the devastating cyber attacks and ever-advancing hackers, especially for startups has never been easier. With startups becoming the worst victims of cyber crime, we think cyber terrorism is nowhere less to the recent Pakistan Taliban school attack. The attack had killed over 140 innocent people including 132 students of an army school located in Peshawar. Sure, ransomware doesn’t cause any deaths but due to it, companies go down, people lose jobs and they end up on the road (not an exaggeration!).
Ransomware has been a growing trend for the past two years, and this is just a culmination, a grand reveal to the wider world of just how big of a threat it is. As we write, someone is clicking a link in a spam email or activating macros in a malicious document.
In a few seconds, all their data will be encrypted and they’ll have just a few days (or even lesser) to pay hundreds of dollars to get it back. Unless they have a backup, which most people don’t.
It’s not just the big shot companies which are in e-Commerce space, retail, or IT industry that are experiencing a blip down in a blaze of loss with cyber attacks, but many startups are also the victims. The smart minds, the fresh techies are being brainwashed and being assessed in the cyber terrorism like ransomware.
How intensive is the cyber threat for startups?

First, the cyber hackers’ targeted website might notice a denial of service (DOS) attack, where the network resource is made unavailable to users. There will also be a slow down in their web traffic, temporary suspension or interruption of a host connected to the web, eventually flooding the traffic resource with unauthorized scripts and external communication requests. And we all witnessed the massive attack by the ransomware WannaCry that I cited above.
As a result of this malicious attack, the system doesn’t respond as before. The bots sent by hackers would trigger a temporary error in the machine, forcing the system to experience new vulnerabilities like increasing the overloading time, stopping the legitimate web-traffic and crashing the server altogether. Worse, sometimes the entire website automatically gets redirected to deceitful web space or an irrelevant website, thereby making a genuine website look spam.
These scenarios may sound like unimportant but eventually within a day or two after the malicious attack on a targeted website by scripted bots, traffic comes down consistently and harms the website much more. In India, the ransomware WannaCry, the biggest ever cyber terrorism attack had infected 45,000 computers, including 120 Gujarat Govt. Computers.
FIGHTING cyber terrorism
Did you know?
The massive, worldwide ransomware attack was stopped by a researcher ‘accidentally’.
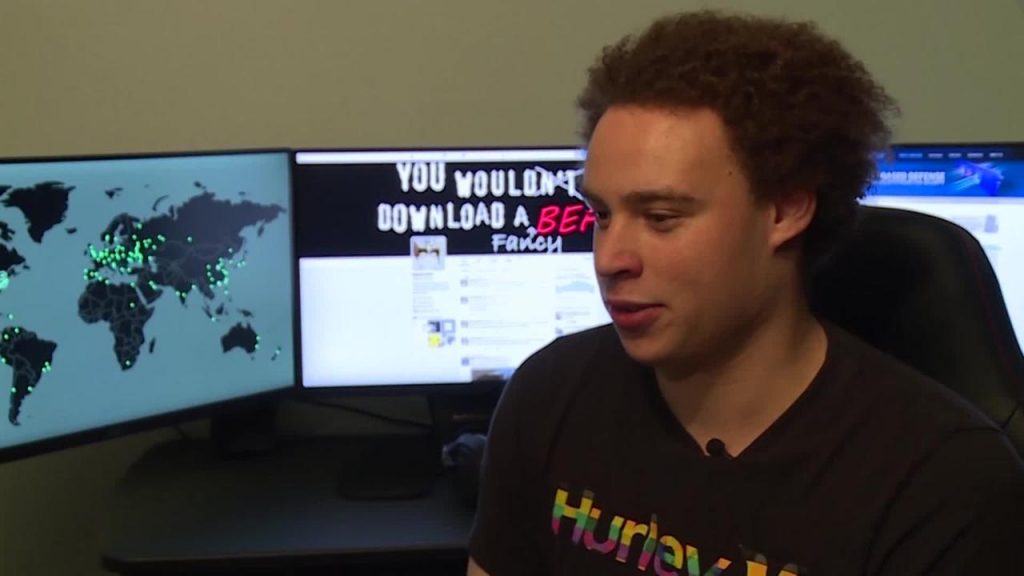
A young British security researcher, Marcus Hutchins has been credited with stopping the WannaCry ransomware attack from spreading across the globe by accidentally triggering a “kill switch”. You can read a detailed version of what happened here at the researcher’s website, MalwareTech.
This is what he had to say on world’s biggest cyber terrorism – ransomware,
“All this code is doing is attempting to connect to the domain we registered and if the connection is not successful it ransoms the system…my registration of it caused all infections globally to believe they were inside a sandbox and exit…thus we initially unintentionally prevented the spread and and further ransoming of computers infected with this malware.”
Some incredible yet simple things you can do to prevent cyber terrorism

Not much about the cyber attacker is known, other than that they could be a potential competitor or fraudulent who attempted to extract money from you. We still recommend you to follow these simple things that can protect your data from hackers and protect company’s privacy on the whole.
Strong password protection
Always choose to password protect your devices or systems to drive hackers away. According to security experts, an ideal password should be more in length, involving special characters and preferably the combination of symbols, numbers, lower/upper case letters than a simple text.

Encrypt your computer
Not only can this halt cyber criminals and stop dangerous malwares like ransomware, but you can be pretty much confident of your content being shared with only authenticated persons. Encrypting your system, machine or admin means only people who have an encryption key provided by you can access it. If you have not encrypted your computer yet, go to your system settings and do it right away.
Keep your anti-malware programs and antivirus up-to-date
These simple little steps that protect intruding malwares and viruses from reaching your system and turning it into a security fob. Hackers keep stepping into a new game with advanced malware programs by releasing new viruses, keyloggers, trojan horses, worms and many other forms of malware that attack your server, system or computer. So it is essential that you follow the security updates and keep your anti-malware and antivirus software up to date.
Also, it is recommended to use Norton antivirus for PC to keep it safe and secure. However, you may be worried about the expensive nature. Not anymore! We are offering deals for the customers who are willing to make a purchase. Use exclusive norton coupon code during the payment checkout process to get maximum discounts.

Clear system’s cookies on a regular basis
Do you clear your system’s cookies on a regular basis? If you just shrugged, then I am worried about your system data and you should be too. Change your system browser settings to clear automatically after every session. Chances that you can reduce the amount of tracking of your online behaviour by hackers go higher if you keep clearing the cookies.
Remove data from your system that you no longer use
Any sensitive or confidential information stored on your computers or systems that you no longer use has to be removed. Consider a plan to remove this unwanted sensitive information safely from your company systems. Even though it’s not useful to you anymore, it can harm you in so many ways if this data falls into the wrong hands. Because you still have a responsibility as an entrepreneur to keep your former employees, clients or contractors’ information safe from web criminals.
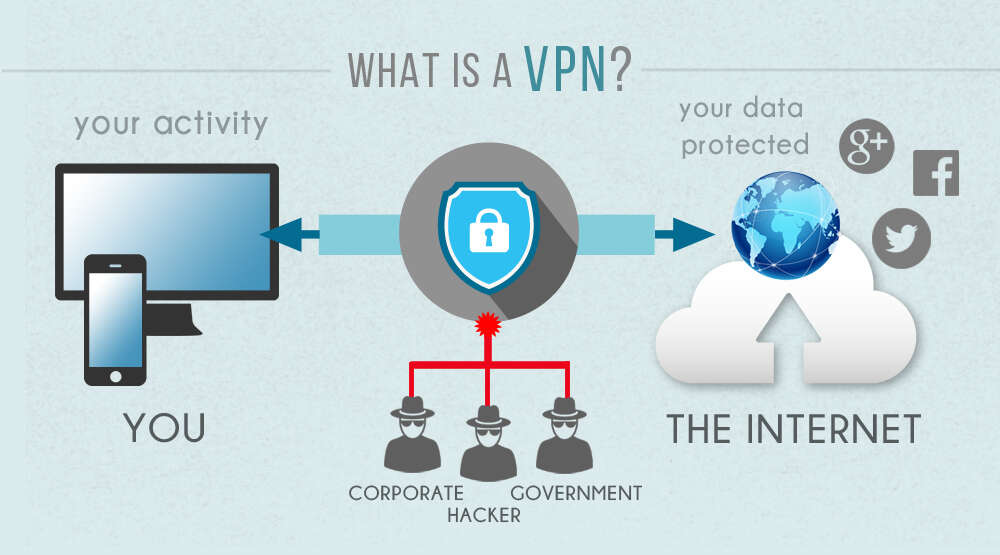
Use a virtual private network (VPN) service
So your company’s system probably contains highly-confidential data that you would not want stolen. Accessing the web with weak security Wi-Fi, or public networks means you’re vulnerable to web attack from cybercriminals. So the best way to prevent hackers from accessing your information and data from your computer when accessing the web via Wi-Fi is to use a virtual private network service. This network service will automatically encrypt all your web communications, thereby protecting your company’s or system’s confidential data.
Here’s an excerpt from an article written by FBI Director, Robert S. Mueller, III
Let me begin with cyber threats to our national security. Terrorists are increasingly cyber savvy. Much like every other multi-national organization, they are using the Internet to grow their business and to connect with like-minded individuals. And they are not hiding in the shadows of cyber space. Al Qaeda in the Arabian Peninsula has produced a full-color, English-language online magazine. They are not only sharing ideas, they are soliciting information and inviting recruits to join al Qaeda. Al Shabaab—the al Qaeda affiliate in Somalia—has its own Twitter account. Al Shabaab uses it to taunt its enemies—in English—and to encourage terrorist activity. Extremists are not merely making use of the Internet for propaganda and recruitment. They are also using cyber space to conduct operations.
As in the words of the FBI Director and we quote – We must use our connectivity to stop those who seek to do us harm. Cyber terrorism is growing at large and needs to be stopped immediately.
While cyber cells and ethical hackers continue to work on it, we can make tiny efforts on our own by getting anti-malware and anti-virus software such as McAfee. And here are some McAfee coupons to help you save money on your purchase.
Image Courtesy:
ibmjournal.com
hackmageddon.com
blog.talosintelligence.com
blogs.metricstream.com
independent.co.uk
gogeekyourself.blogspot.in
pinterest.com
vox.com
aboutvpns.com